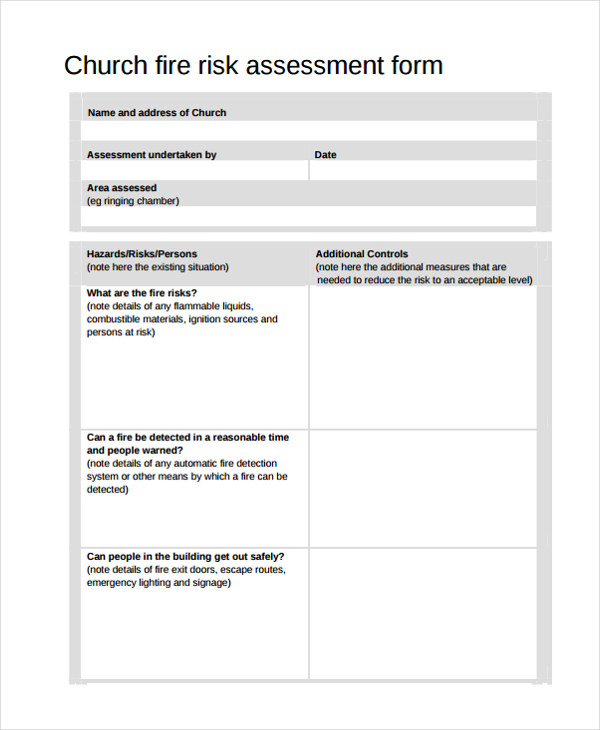
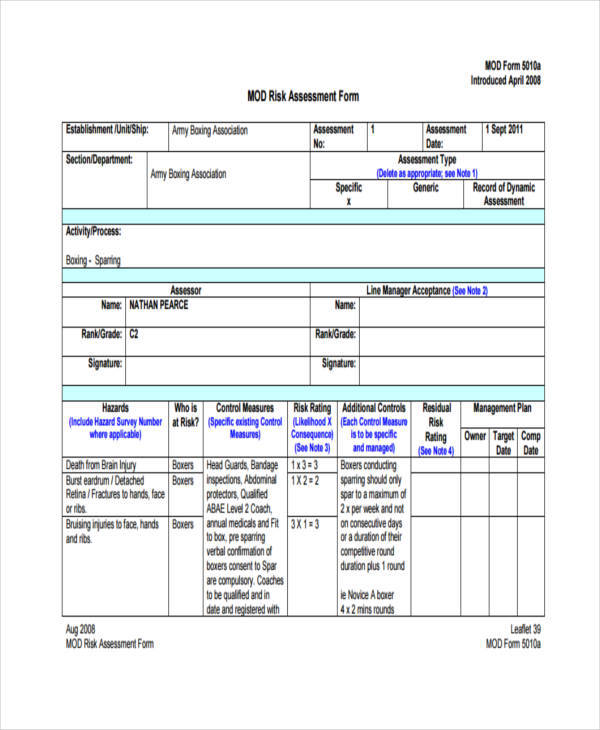
Risk Acceptance Form
Risk Acceptance Form - Web here are key elements offered by experts to help cisos get risk acceptance right: The system/project manager is responsible for writing the justification and the compensating control. Web instructions for risk acceptance form. If the cost of other risk responses exceeds the value that would be gained, a. Web simply put, risk acceptance is a status quo risk response. Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. Web risk acceptance form responsible individual’s information summary of request (risk to be accepted). E., risk working group [rwg] and executive risk committee [erc], erm liaisons and individuals that support the implementation and operation of erm at the irs). Summary of how doing this will put uc at risk: Web form & templates.
E., risk working group [rwg] and executive risk committee [erc], erm liaisons and individuals that support the implementation and operation of erm at the irs). Cms information security policy/standard risk acceptance template of the rmh chapter 14 risk assessment. Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. If the cost of other risk responses exceeds the value that would be gained, a. In addition, the risk acceptance form has been placed onto the cms fisma controls tracking system (cfacts). Web instructions for risk acceptance form. Summary of information security controls: The system’s business owner is responsible for writing the justification and the compensating control or remediation plan. Please complete all risk acceptance forms under the risk acceptance. It is a requirement that a compensating control be defined in order to obtain full approval for a.
Web this form is to be used to justify a risk acceptance of a known deficiency. Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. Benefits of accepting this risk: Summary of information security controls: In addition, the risk acceptance form has been placed onto the cms fisma controls tracking system (cfacts). Cms information security policy/standard risk acceptance template of the rmh chapter 14 risk assessment. It is a requirement that a compensating control be defined in order to obtain full approval for a. Web risk acceptance form responsible individual’s information summary of request (risk to be accepted). Please complete all risk acceptance forms under the risk acceptance. Web form & templates.
Risk assessment form Template New Sample Risk assessment form 18 Free
Web risk acceptance form (raf) for assistance in completing this form please see the following link: Please complete all risk acceptance forms under the risk acceptance. Web here are key elements offered by experts to help cisos get risk acceptance right: The system/project manager is responsible for writing the justification and the compensating control. Benefits of accepting this risk:
Information Risk Acceptance Process
Web this form is to be used to document, justify and formally accept risk for a known deficiency(ies). Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. Web risk acceptance form (raf) for assistance in completing this form please see the following link: The system/project manager is responsible for writing the justification.
Risk Acceptance Form Threat Vulnerability
Summary of how doing this will put uc at risk: The system’s business owner is responsible for writing the justification and the compensating control or remediation plan. Know what’s most important to your organization the ciso must understand which risks pose what concerns to have. It is a requirement that a compensating control be defined in order to obtain full.
Risk Acceptance Request University of Cincinnati
Summary of information security controls: Description of the type of data that will be associated with the risk specifically (hipaa, ferpa or pci). In addition, the risk acceptance form has been placed onto the cms fisma controls tracking system (cfacts). The system’s business owner is responsible for writing the justification and the compensating control or remediation plan. Web risk acceptance.
26+ Risk Assessment Form Templates
Please complete all risk acceptance forms under the risk acceptance. Raf field descriptions name, title, and department of originator: The agency/division is responsible for writing the justification and identifying the compensating control. The system’s business owner is responsible for writing the justification and the compensating control or remediation plan. The system/project manager is responsible for writing the justification and the.
Acknowledgement Of Risks Acceptance Of Responsibility Form printable
Raf field descriptions name, title, and department of originator: The system’s business owner is responsible for writing the justification and the compensating control or remediation plan. Web this form is to be used to justify a risk acceptance of a known deficiency. Risk owners acknowledge the risk exists but accept the risk with minimal response. It is a requirement that.
Information Risk Acceptance Process
Web risk acceptance form (raf) for assistance in completing this form please see the following link: Web instructions for risk acceptance form. Web 1) a framework to assess various options in making decisions for achievement of objectives, 2) a guide to articulate rationale behind those decisions within the context of risk appetite, and 3) a documentation trail. Summary of information.
FREE 37+ Risk Assessment Forms in PDF MS Word
Summary of information security controls: Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. Summary of how doing this will put uc at risk: Benefits of accepting this risk: Benefits of accepting this risk:
ENGAGEMENT ACCEPTANCE FORM
Web 1) a framework to assess various options in making decisions for achievement of objectives, 2) a guide to articulate rationale behind those decisions within the context of risk appetite, and 3) a documentation trail. Benefits of accepting this risk: Web this form is to be used to justify a risk acceptance of a known deficiency. Description of the type.
Risk Acceptance 23905 Risk Reliability Engineering
Web simply put, risk acceptance is a status quo risk response. Cms information security policy/standard risk acceptance template of the rmh chapter 14 risk assessment. Web this form is to be used to justify a risk acceptance of a known deficiency. Web 1) a framework to assess various options in making decisions for achievement of objectives, 2) a guide to.
Web 1) A Framework To Assess Various Options In Making Decisions For Achievement Of Objectives, 2) A Guide To Articulate Rationale Behind Those Decisions Within The Context Of Risk Appetite, And 3) A Documentation Trail.
Cms information security policy/standard risk acceptance template of the rmh chapter 14 risk assessment. Web instructions for risk acceptance form. If the cost of other risk responses exceeds the value that would be gained, a. Web this form is to be used to justify a risk acceptance of a known deficiency.
The Agency/Division Is Responsible For Writing The Justification And Identifying The Compensating Control.
Web risk acceptance form (raf) for assistance in completing this form please see the following link: Summary of how doing this will put uc at risk: It is a requirement that a compensating control be defined in order to obtain full approval for a. Summary of information security controls:
Web Simply Put, Risk Acceptance Is A Status Quo Risk Response.
Web here are key elements offered by experts to help cisos get risk acceptance right: Web this form is to be used to document, justify and formally accept risk for a known deficiency(ies). Benefits of accepting this risk: Benefits of accepting this risk:
Web Risk Acceptance Form Responsible Individual’s Information Summary Of Request (Risk To Be Accepted).
Web throughout this irm section, “the erm program” refers collectively to the erm processes, governance bodies (i. Know what’s most important to your organization the ciso must understand which risks pose what concerns to have. Raf field descriptions name, title, and department of originator: Risk owners acknowledge the risk exists but accept the risk with minimal response.